We are living in an era dominated by digital connectivity. You can’t overstate the importance of cybersecurity. As technology advances, so do the threats that lurk in the online world.
Often, it’s our own actions that leave us most at risk of a cyberattack or online scam. Risky behaviors include weak passwords and lax security policies. As well as thinking “This won’t happen to me.” This is why human error is the cause of approximately 88% of data breaches.
The National Cybersecurity Alliance and CybSafe are working to correct poor cyber hygiene. Each year, the duo publishes a report on cybersecurity attitudes and behaviors. The goal is to educate both people and businesses. To educate them on how to better secure their digital landscapes.
This year’s study surveyed over 6,000 people across the U.S., Canada, the U.K., Germany, France, and New Zealand. The survey asked about several things. These include knowledge of cybersecurity risks, security best practices, and challenges faced.
The report reveals some eye-opening insights. These include how people perceive and respond to cyber threats. As well as what they can do to improve their cybersecurity posture. Here are some of the key findings from the report.
We Are Online… a Lot
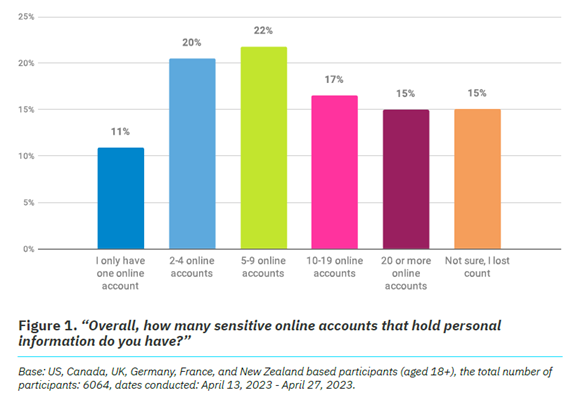
It’s no surprise that 93% of the study participants are online daily. The logins we create continue to expand, as well as those considered “sensitive.” Sensitive accounts hold personal information that could be harmful if stolen.
Nearly half (47%) of the study’s respondents have ten or more sensitive online accounts. This amplifies risk. Especially if people are using the same password for two or more of those accounts.
Online Security Makes People Frustrated
Most people (84%) feel that online security is a priority. But as many as 39% feel frustrated, and nearly the same amount intimidated. It can seem that you just can’t get ahead of the hackers. Just over half of people thought digital security was under their control. That leaves a whole lot that don’t think so.
But that is no reason to let down your defenses and become an easy target. There are best practices you can put in place to safeguard your online accounts that work.
These include:
- Enabling multi-factor authentication on your accounts
- Using an email spam filter to catch phishing emails
- Adding a DNS filter to block malicious websites
- Using strong password best practices
People Need More Access to Cybersecurity Training
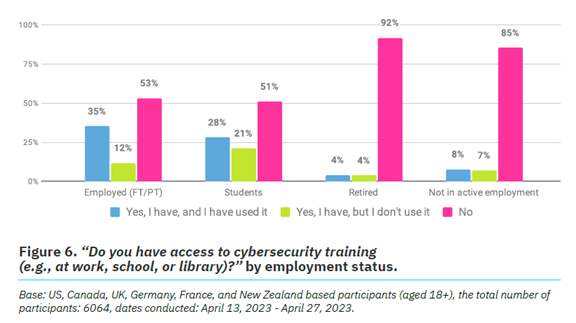
One way to reduce human errors associated with cybersecurity is to train people. The survey found that just 26% of respondents had access to cybersecurity training.
It also broke this down by employment status. We see that those not actively employed are most lacking. Even those employed can use more training access and encouragement. Just 53% report having access to cybersecurity awareness training and using it.
Employers can significantly reduce their risk of falling victim to a data breach. They can do this by beefing up their security awareness training. There is also a large opportunity to provide more training. Particularly to those retired or not actively employed.
Cybercrime Reporting Is Increasing
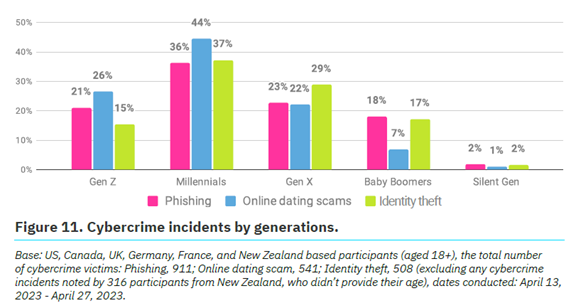
Over a quarter (27%) of survey participants said they had been a victim of cybercrime.
The types of cybercrimes reported include:
- Phishing (47%)
- Online dating scams (27%)
- Identity theft (26%)
Which generation reported the most cybercrime incidents? Millennials. In fact, Baby Boomers and the Silent Generation reported the fewest.
No matter where you fall in the generations, it’s important to adopt security best
practices. We’ll go through some of these next.
Online Security Best Practices to Reduce Your Risk
- Strong, Unique Passwords:
- Start with the basics. Create strong, unique passwords for each online account.
- Use a combination of uppercase and lowercase letters, numbers, and special characters.
- Multi-Factor Authentication (MFA):
- Enhance your account security with multi-factor authentication.
- MFA adds an extra barrier to unauthorized access. Even for
compromised passwords.
- Regular Software Updates:
- Keep all your software, including operating systems and mobile
apps, up to date.
- Keep all your software, including operating systems and mobile
- Beware of Phishing Attacks:
- Exercise caution when clicking on links or opening attachments
especially in emails from unknown sources. - Verify the legitimacy of emails and websites. Check for subtle
signs, such as misspelled URLs or unfamiliar sender addresses.
- Exercise caution when clicking on links or opening attachments
- Use Secure Wi-Fi Networks:
- Ensure you connect to a secure and password-protected Wi-Fi
network. - Avoid using public Wi-Fi for sensitive transactions. Unless using a virtual private network (VPN).
- Ensure you connect to a secure and password-protected Wi-Fi
- Data Backup:
- Regularly back up important data to an external device or a secure
cloud service.
- Regularly back up important data to an external device or a secure
- Use Antivirus and Anti-Malware Software:
- Install reputable antivirus and anti-malware software on all devices.
- Regularly scan your systems for potential threats.
- Be Mindful of Social Media Settings:
- Review and adjust your privacy settings on social media platforms.
- Limit the amount of personal information visible to the public.
- Secure Your Personal Devices:
- Lock your devices with strong passwords or biometric
authentication.
- Lock your devices with strong passwords or biometric
- Educate and Stay Informed:
- Educate yourself and your team through cybersecurity awareness
programs. This fosters a culture of vigilance and preparedness.
- Educate yourself and your team through cybersecurity awareness
Schedule Cybersecurity Awareness Training Today
A little education on cybersecurity goes a long way toward protecting your data. Our experts can provide security training at the level you need. We’ll help you fortify your defenses against phishing, scams, and cyberattacks.
Contact us today to schedule a chat.
This Article has been Republished with Permission from The Technology Press.
Recent Blogs
Related posts
What You’re Missing in Microsoft 365 (Without an Audit)
If your business uses Microsoft 365, there's a good chance you're not getting everything you're paying for. Like most people, you might assume your setup [...]
Wi-Fi Performance Secrets to Boost Your Business Productivity
Nothing disrupts your workday quite like unreliable Wi-Fi. One moment everything’s running smoothly, and the next, video calls freeze, files won’t upload, and the team [...]
Project Chaos to Clarity: How Microsoft Planner Transforms Small Businesses
In the past, teams relied on sticky notes and endless email threads to manage tasks. But with today’s hybrid work environments and fast-moving deadlines, that [...]